Ping sweeping is a basic technique to find active hosts on a network.
You might be looking for a particular host in your infrastructure, like a network printer, or you simply want to assign a static IP to a new network host/device and want to know which IP is free to use.
As an example, we want to scan our whole subnet: 192.168.1.0/24.
That means we need to run through all the 254 hosts, from 192.168.1.1 to 192.168.1.254, ping them and return only the addresses that were responding to our queries.
In Unix-type systems, like Linux, BSD and macOS we use the bash shell which is available in all those operating systems. When using Windows, it's cmd which is the native built-in command line utility.
A for loop iterates through all the possible host addresses, pings them and prints out the active hosts only.
Note that we use the 192.168.1.0/24 subnet with 254 hosts, but we could easily specify a bigger or smaller subnet, modifying our commands.
For example, if we want to scan 10.0.0.0/27, which is all the hosts from 10.0.0.1 to 10.0.0.30 we'd modify the for loop accordingly. We also can scan irregular ranges, not needing to cover whole subnets.
Don't forget to modify the ping command, use your specific subnet if it differs from 192.168.1.x
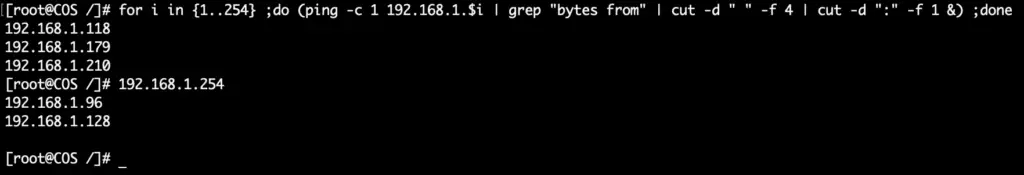
Bash (linux, Mac, BSD)
for i in {1..254} ;do (ping -c 1 192.168.1.$i | grep "bytes from" &) ;done
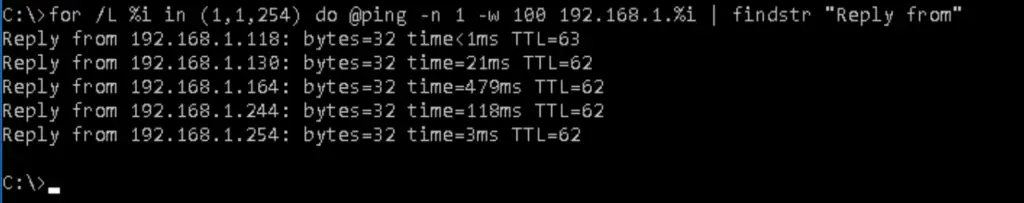
Cmd (Windows)
for /L %i in (1,1,254) do @ping -n 1 -w 100 192.168.1.%i | findstr "Reply from"
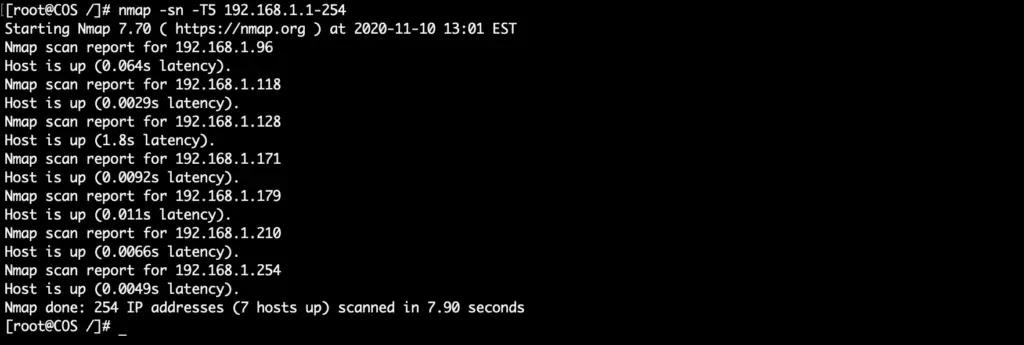
Nmap
And finally the classic Nmap command for ping sweeping
nmap -sn -T5 100 192.168.1.1-254
Enjoy 🙂

Comments