Change the jd0e.com MX record to point to the agzsolt.com on-prem server
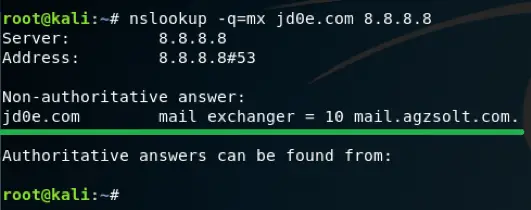
Because of this change the incoming mails to @jd0e.com will be directed to the mail.agzsolt.com server where the migrated mailboxes will sit or if no local mailbox is found by the server it forwards them to the cloud where the cloud servers will find the route to the correct tenant.
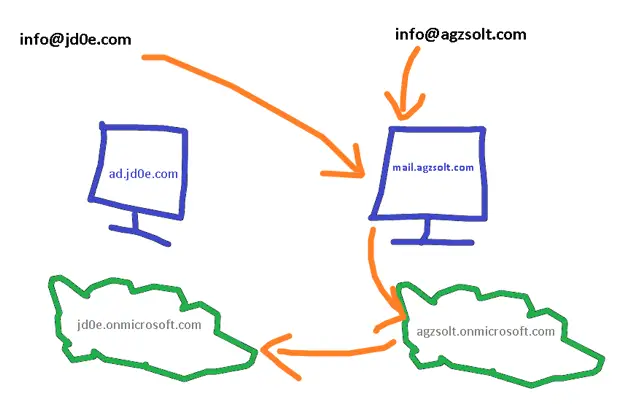
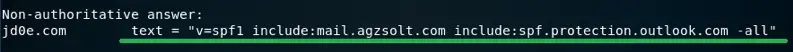
Now test the mail flow to verify the emails are still arriving to the @jd0e.com mailboxes: we send an email from a Gmail address to a jd0e.com mailbox. Note that the jd0e.com MX record has already been changed to the destination on-prem server (mail.agzsolt.com). Also the SPF record is updated accordingly to prevent the sent emails to be put in the recipient’s junk folder.
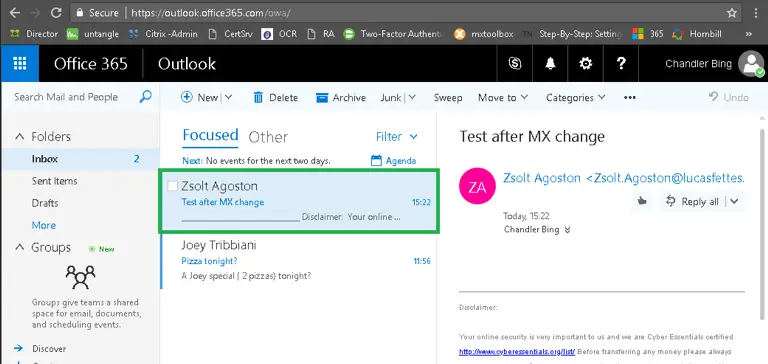
The email has arrived without an issue!
Disable Federation
First we need to disable ADFS before we can proceed and cut dirsync to make the mailboxes fully cloud-managed.
Let’s see how the OWA portal behaves. As soon as we try to log in on https://outlook.office365.com it redirects us to the local ADFS proxy server for authentication
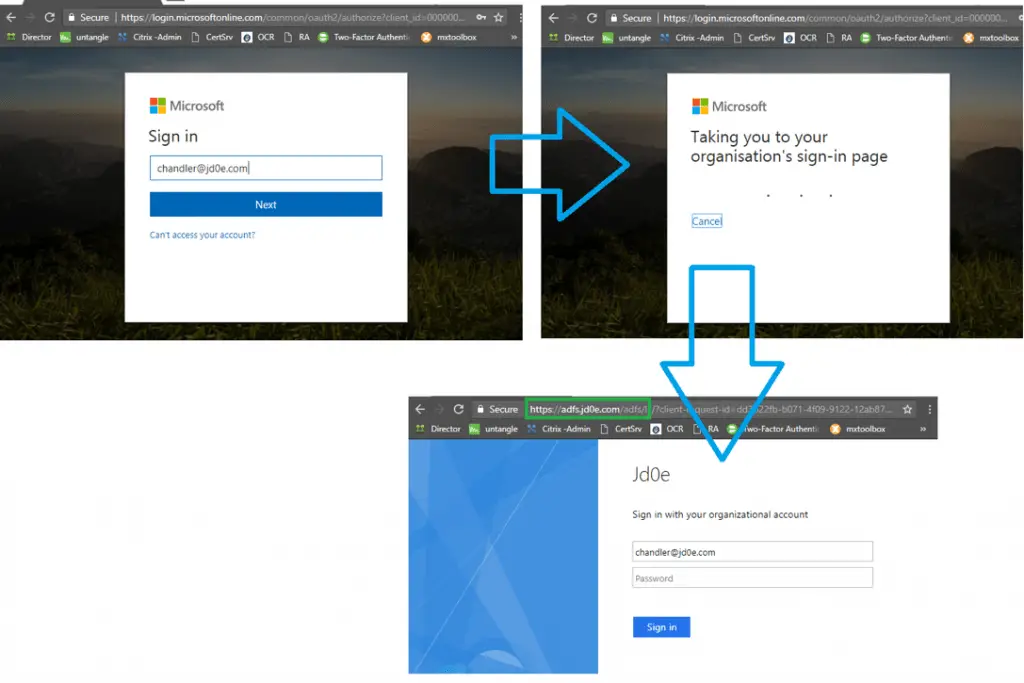
We can see on dc.jd0e.com server that the domain is federated:
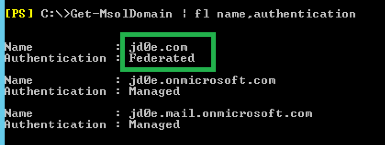
Now we make the domain standalone. First we connect to the ADFS server
Set-MsolADFSContext -Computer adfs.jd0e.com
And set the domain to standard:
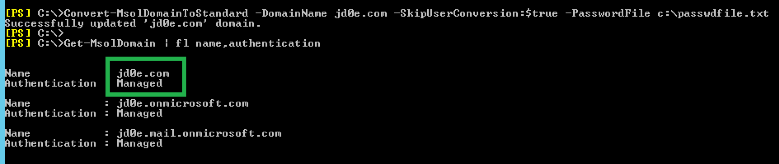
Convert-MsolDomainToStandard -DomainName jd0e.com -SkipUserConversion:$true -PasswordFile c:\passwdfile.txt
Setting the authentication method as well:
Set-MsolDomainAuthentication -Authentication managed -DomainName jd0e.com
At this point the domain becomes cloud-managed again, that we will confirm
To see if the authentication works we check the login interface again:
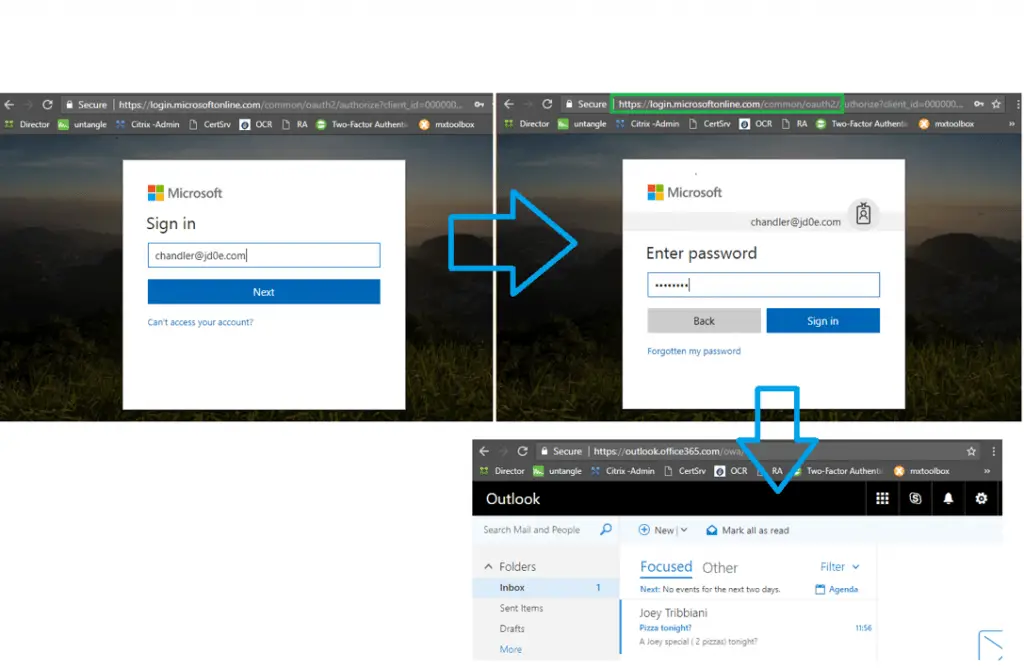
We are in, the authentication is happening in the cloud with the AD password that is synced with DirSync! Excellent!
