Our goal is to make our website protected, configuring the HTTPS service on it to ensure encrypted traffic between the client and our server. We utilize Let’s Encrypt’s certbot, that will create and automatically renew the publicly signed SSL certificates for our site or multiple sites.
Before You Begin
We start with a basic webserver already configured on a CentOS box, and we assume the server is accessible publicly on the http and https ports. This is needed for the certbot agent to verify our domain ownership, otherwise the certificate deployment fails.
For a detailed guide on how to install a webserver on CentOS 8, click HERE 🙂
1. Install and run Certbot
It is a little more manual than on Debian or Ubuntu (see HERE), we need to download the certbot binary and run it manually. The binary will install all the prerequisits for us, then acquire the certificate for us, setting the virtual hosts up. We only need to create a scheduled task manually to ensure it is automatically renewed every three months.
Now start with downloading and running Certbot
sudo curl -O https://dl.eff.org/certbot-auto
sudo mv certbot-auto /usr/local/bin
sudo chmod 755 /usr/local/bin/certbot-auto
# Run Certbot for protectigate.com only.
sudo certbot-auto --apache -d protectigate.com -d www.protectigate.com
All the required packages will be installed, then the cert configuration starts.
Saving debug log to /var/log/letsencrypt/letsencrypt.log
Plugins selected: Authenticator apache, Installer apache
Enter email address (used for urgent renewal and security notices) (Enter 'c' to
cancel): zsolt@opentechtips.com
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Please read the Terms of Service at
https://letsencrypt.org/documents/LE-SA-v1.2-November-15-2017.pdf. You must
agree in order to register with the ACME server at
https://acme-v02.api.letsencrypt.org/directory
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(A)gree/(C)ancel: A
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Would you be willing to share your email address with the Electronic Frontier
Foundation, a founding partner of the Let's Encrypt project and the non-profit
organization that develops Certbot? We'd like to send you email about our work
encrypting the web, EFF news, campaigns, and ways to support digital freedom.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(Y)es/(N)o: N
Obtaining a new certificate
Performing the following challenges:
http-01 challenge for protectigate.com
http-01 challenge for www.protectigate.com
Waiting for verification...
Cleaning up challenges
Created an SSL vhost at /etc/httpd/conf.d/protectigate.com-le-ssl.conf
Deploying Certificate to VirtualHost /etc/httpd/conf.d/protectigate.com-le-ssl.conf
Deploying Certificate to VirtualHost /etc/httpd/conf.d/protectigate.com-le-ssl.conf
Please choose whether or not to redirect HTTP traffic to HTTPS, removing HTTP access.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
1: No redirect - Make no further changes to the webserver configuration.
2: Redirect - Make all requests redirect to secure HTTPS access. Choose this for
new sites, or if you're confident your site works on HTTPS. You can undo this
change by editing your web server's configuration.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Select the appropriate number [1-2] then [enter] (press 'c' to cancel): 2
Redirecting vhost in /etc/httpd/conf.d/protectigate.com.conf to ssl vhost in /etc/httpd/conf.d/protectigate.com-le-ssl.conf
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Congratulations! You have successfully enabled https://protectigate.com and
https://www.protectigate.com
You should test your configuration at:
https://www.ssllabs.com/ssltest/analyze.html?d=protectigate.com
https://www.ssllabs.com/ssltest/analyze.html?d=www.protectigate.com
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
IMPORTANT NOTES:
- Congratulations! Your certificate and chain have been saved at:
/etc/letsencrypt/live/protectigate.com/fullchain.pem
Your key file has been saved at:
/etc/letsencrypt/live/protectigate.com/privkey.pem
Your cert will expire on 2020-07-10. To obtain a new or tweaked
version of this certificate in the future, simply run certbot-auto
again with the "certonly" option. To non-interactively renew *all*
of your certificates, run "certbot-auto renew"
- Your account credentials have been saved in your Certbot
configuration directory at /etc/letsencrypt. You should make a
secure backup of this folder now. This configuration directory will
also contain certificates and private keys obtained by Certbot so
making regular backups of this folder is ideal.
- If you like Certbot, please consider supporting our work by:
Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate
Donating to EFF: https://eff.org/donate-le
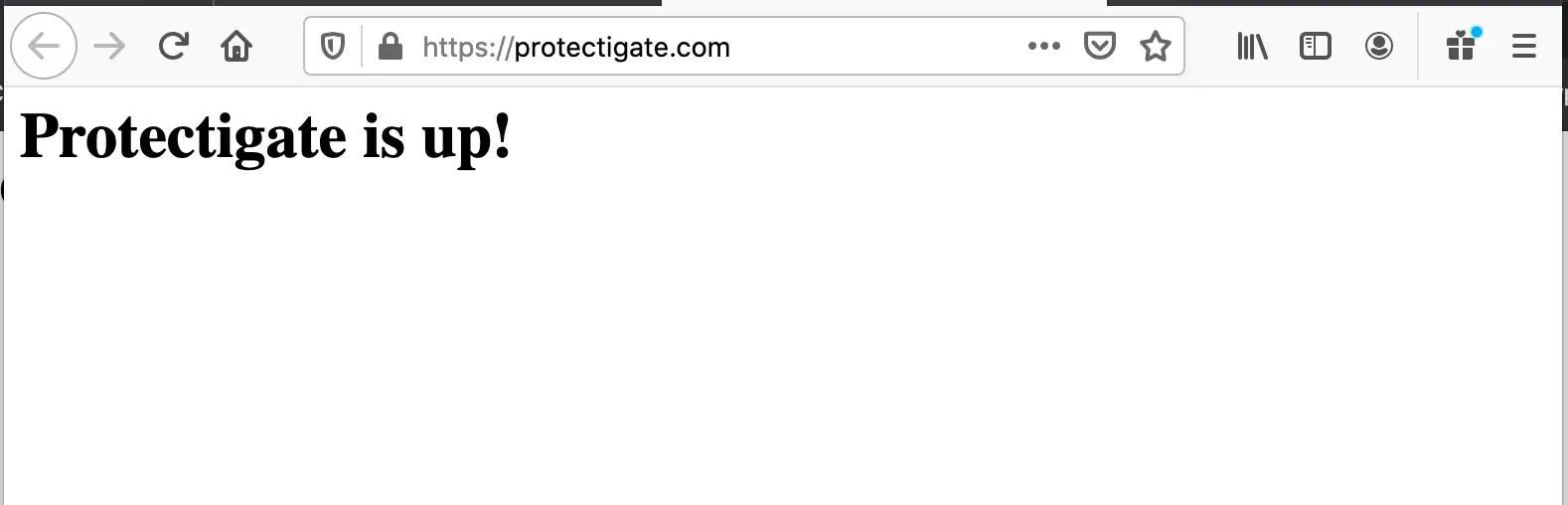
Now we can browse to the website we confirm that it is working and is protected
Automatize the SSL renewal
A cron job needs to be added to the server so it will check every 12 hours if the certificates are due to renew, if they are, they are auto-renewed
crontab -e
echo "0 0,12 * * * root python3 -c 'import random; import time; time.sleep(random.random() * 3600)' && /usr/local/bin/certbot-auto renew -q" | sudo tee -a /etc/crontab > /dev/null
Aftermath
If you check you see that Certbot modified the original protectigate.com.conf file, adding auto-forwarding to HTTPS://protectigate.com
john@web:/etc/httdp/conf.d/ $ cat protectigate.com.conf
<VirtualHost *:80>
DocumentRoot /var/www/protectigate.com
ServerName protectigate.com
ServerAlias www.protectigate.com
RewriteEngine on
RewriteCond %{SERVER_NAME} =protectigate.com [OR]
RewriteCond %{SERVER_NAME} =www.protectigate.com
RewriteRule ^ https://%{SERVER_NAME}%{REQUEST_URI} [END,NE,R=permanent]
</VirtualHost>
A new protectigate.com-le-ssl.conf file is created for the HTTPS configuration
<IfModule mod_ssl.c>
<VirtualHost *:443>
DocumentRoot /var/www/protectigate.com
ServerName protectigate.com
ServerAlias www.protectigate.com
Include /etc/letsencrypt/options-ssl-apache.conf
SSLCertificateFile /etc/letsencrypt/live/protectigate.com/fullchain.pem
SSLCertificateKeyFile /etc/letsencrypt/live/protectigate.com/privkey.pem
</VirtualHost>
</IfModule>

Comments