Zimbra, like all secure servers that communicate on the internet, needs a publicly trusted SSL certificate to function correctly. Both client access and secure SMTP mail transmission depend on the SSL certificate, which is by default self-signed when the installation of a fresh server finishes.
This provides encryption from the very get-go, but being self-issued it is not trusted by other servers on the internet which causes warning messages for users when opening the access portal, and partner organizations possibly rejecting our emails as many email servers require perfectly functioning TLS encryption to send and receive messages.
We need a new certificate, signed by a public certification authority. There are many CAs out there that we can use, but we want to save money and get our SSL certificate for free.
Let's Encrypt offers free certificates valid for 3 months, after which they are free to renew. We already covered how to get LE certificates for CentOS boxes, this time we incorporate that knowledge into a script to get and automatically renew the SSL certificate for our Zimbra server running on CentOS 8 ( for the installation guide click here ) Let's get started!
1. Install the Let's Encrypt Certbot
# Install Certbot on the linux box yum install -y certbot # Generate our first SSL cert. Subsequent certificates will be renewed by our script below certbot certonly --standalone -d mail.protectigate.com -m zsolt@opentechtips.com --agree-tos -n # Prepare the Zimbra directory for the new certificate mkdir /opt/zimbra/ssl/letsencrypt
2. Install the Certificate and create the Script for auto-renewal
a. Create script as /root/ssl.sh
#Change work dir to /tmp
cd /tmp
#Renew cert if needed
certbot certonly --standalone -d mail.protectigate.com -m zsolt@opentechtips.com --agree-tos -n
# Stop the nginx Zimbra service
sudo -u zimbra /opt/zimbra/bin/zmproxyctl stop
sudo -u zimbra /opt/zimbra/bin/zmmailboxdctl stop
#Rename existing Zimbra letsencrypt folder and create new
if [[ -e /opt/zimbra/ssl/letsencrypt ]]; then
mv /opt/zimbra/ssl/letsencrypt /opt/zimbra/ssl/letsencrypt$(date +'%Y%m%d')
mkdir /opt/zimbra/ssl/letsencrypt
chown -R zimbra:zimbra /opt/zimbra/ssl/letsencrypt
fi
# Copy Let's Encrypt SSL cert into Zimbra SSL dir
/bin/cp -rf /etc/letsencrypt/live/mail.protectigate.com/* /opt/zimbra/ssl/letsencrypt/
#Download the Let's Encrypt root cert
wget https://letsencrypt.org/certs/trustid-x3-root.pem.txt -O /opt/zimbra/ssl/letsencrypt/root.pem
#Merge the root cert into the chain file
cat /opt/zimbra/ssl/letsencrypt/root.pem >> /opt/zimbra/ssl/letsencrypt/chain.pem
#Change owner of SSL files to Zimbra user
chown -R zimbra:zimbra /opt/zimbra/ssl/letsencrypt
# Verify new SSL cert
sudo -u zimbra /opt/zimbra/bin/zmcertmgr verifycrt comm /opt/zimbra/ssl/letsencrypt/privkey.pem /opt/zimbra/ssl/letsencrypt/cert.pem /opt/zimbra/ssl/letsencrypt/chain.pem
# Make backup of existing SSL
cp -a /opt/zimbra/ssl/zimbra /opt/zimbra/ssl/zimbra.$(date "+%Y%m%d")
# Copy new priv key
/bin/cp -rf /opt/zimbra/ssl/letsencrypt/privkey.pem /opt/zimbra/ssl/zimbra/commercial/commercial.key
chown zimbra:zimbra /opt/zimbra/ssl/zimbra/commercial/commercial.key
# Install new SSL cert
sudo -u zimbra /opt/zimbra/bin/zmcertmgr deploycrt comm /opt/zimbra/ssl/letsencrypt/cert.pem /opt/zimbra/ssl/letsencrypt/chain.pem
# Restart Zimbra services
sudo -u zimbra /opt/zimbra/bin/zmcontrol restart
b. Make script executable: chmod +x /root/ssl.sh
3. Create cron job to run the script every 3 month
Now that we have our script ready, we create a cron job to run it every month, renewing the certificate if it is about to expire.
#Create new cron job that runs on the 1st every month at 2am (crontab -l && echo "0 2 1 * * /bin/sh /root/ssl.sh") | crontab -
4. Verify
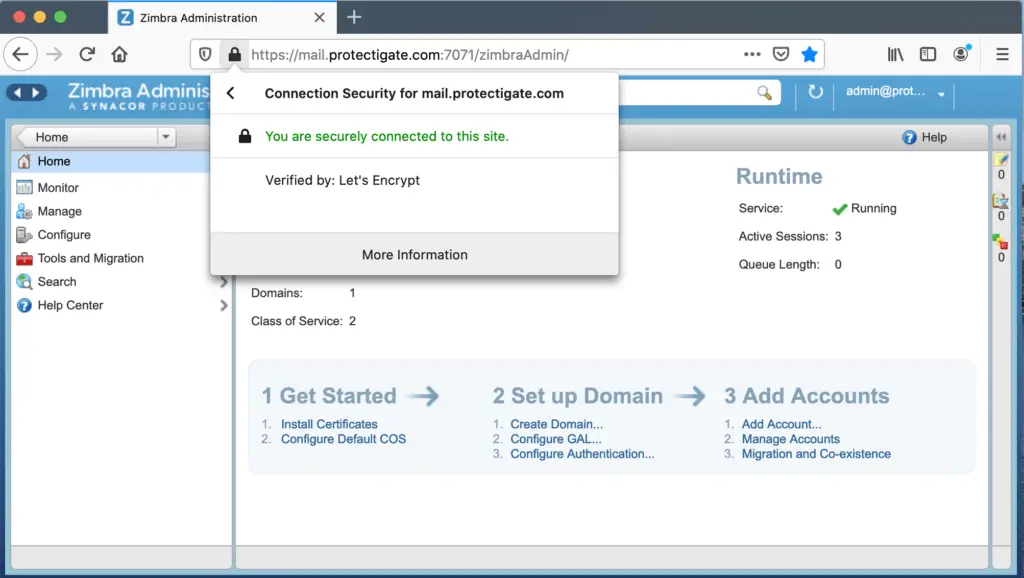
Visiting our management portal the address bar is green, showing that the SSL certificate for our encrypted traffic is trusted. The same applies to the client portal and encrypted SMTP traffic, they are all covered by the new signed key-pair. Enjoy!

These directions do not work for the renewal. The initial creation of the cert works. Renewal fails with authentication errors.
Hi! You find a solution for this?