In our earlier article we went through the history and the ins and outs of the FSMO roles. But how do we know if a FSMO server fails and cannot fulfil it's role?
So What Happens When a FSMO Role Fails?
1. Domain Naming Master
Failure of the server that hold this role is not immediately obvious. This role is only needed when adding or removing domains to or from the forest so if there are no similar changes, the role server can even powered down for an extended period of time, it's absence would not be noticeable.
2. Schema Master
When failing, no changes to the schema can be implemented. Schema changes happen for example when installing a new version of Exchange server in the organization, or upgrading the forest of domain functional levels to a higher level.
3. RID Master
A symptom would be not being able to create new users or joining computers to the domain. However, the domain controllers have an allocated number of RIDs for new accounts, so first they would need to run out of those allocated pool before asking for more from the RID master would failures.
4. PDC Emulator
Probably the failure of this role has the most obvious symptoms, that includes the following:
- password resets don't work in the domain
- accounts are not locking out when trying the wrong password too many times
- GPO changes would not be registered
- computer clocks across the domain are not being synchronized. It can be dangerous as if time on the client computers or servers differ by more than 5 minutes from the authenticator's set time (domain controller), Kerberos would fail on domain joined computers.
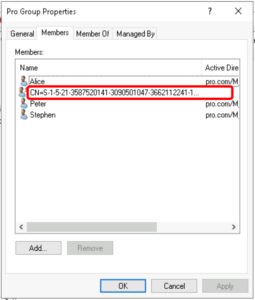
5. Infractructure Master
If failing, in groups or ACLs (security settings in file, folder or AD objects) the long SID would be showing for accounts from other domains, their proper name would not be displayed correctly.

Comments