Opportunistic
Exchange - like most modern email systems - has the facility to transfer email messages encrypted. It is to make sure that messages cannot be read by eavesdroppers in transit. The same time it tries to maintain compatibility with older systems and supports unencrypted traffic too, while preferring encryption when possible.
This is what Exchange calls opportunistic TLS encryption: if both of our email server and the other end supports TLS encryption they will transfer messages in an encrypted fashion. If the other end is a legacy system, our mail server will accommodate and send SMTP messages in clear-text format.
In today's world, when GDPR and other regulations require us to exchange only encrypted messages with a partner, we might need to enforce TLS encryption.
Enforce Outbound TLS
Via PowerShell:
New-SendConnector -Name "ForceTLS" -AddressSpaces "opentechtips.com" -Usage custom -RequireTLS:$true -MaxMessageSize 200MB
Or through the WebUI:
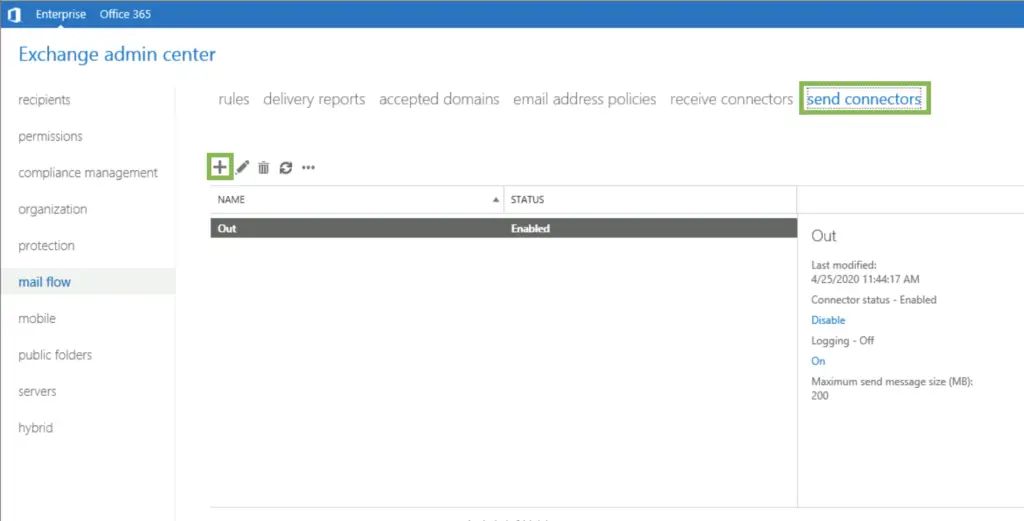
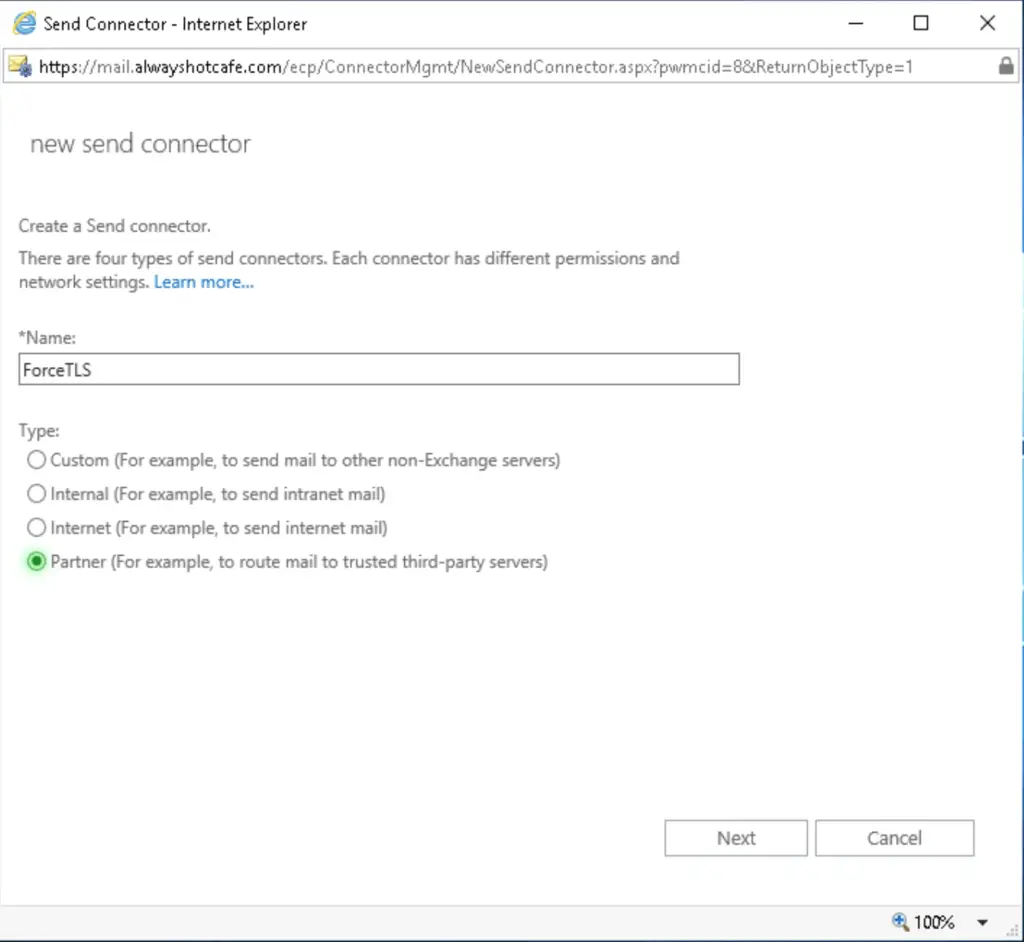
On the WebUI we have to use the "Partner" type as this is the one which enforces TLS. I personally prefer PowerShell where forced TLS can be explicitly specified.
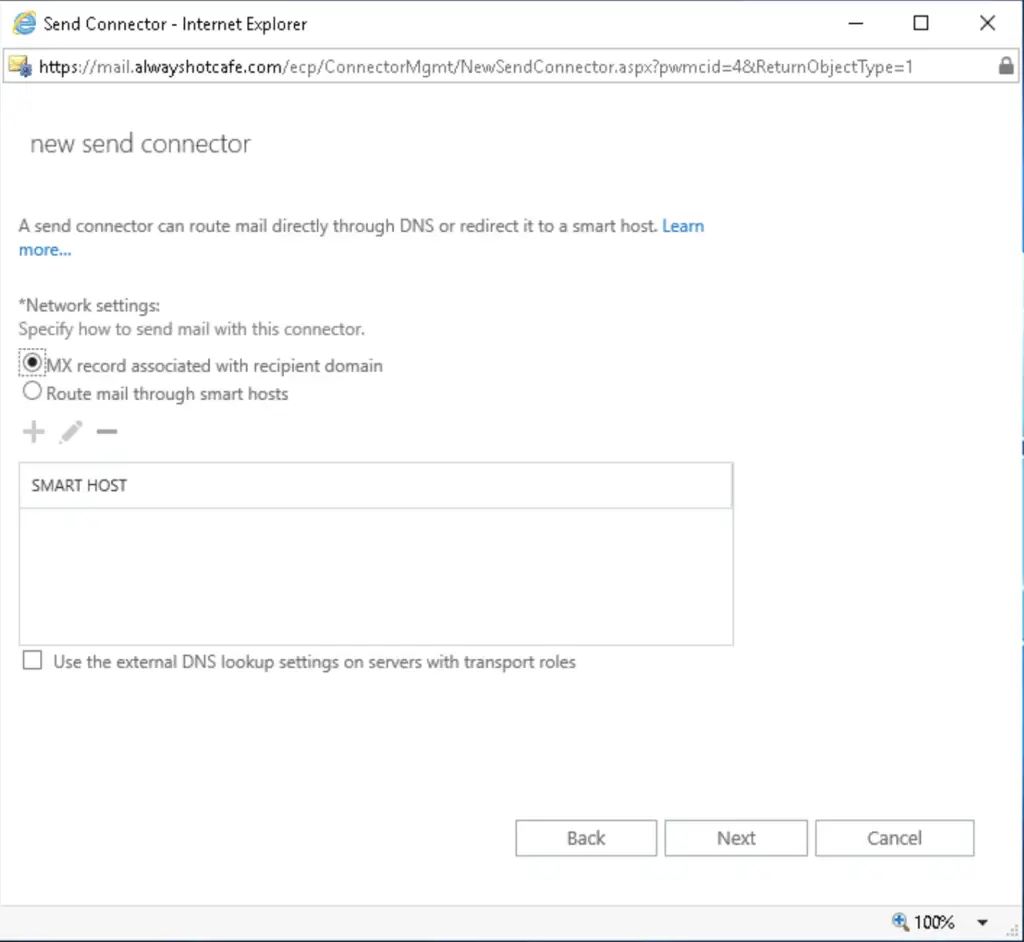
If you use smart hosts, you can set it as the next hop. Here we use MX routing.
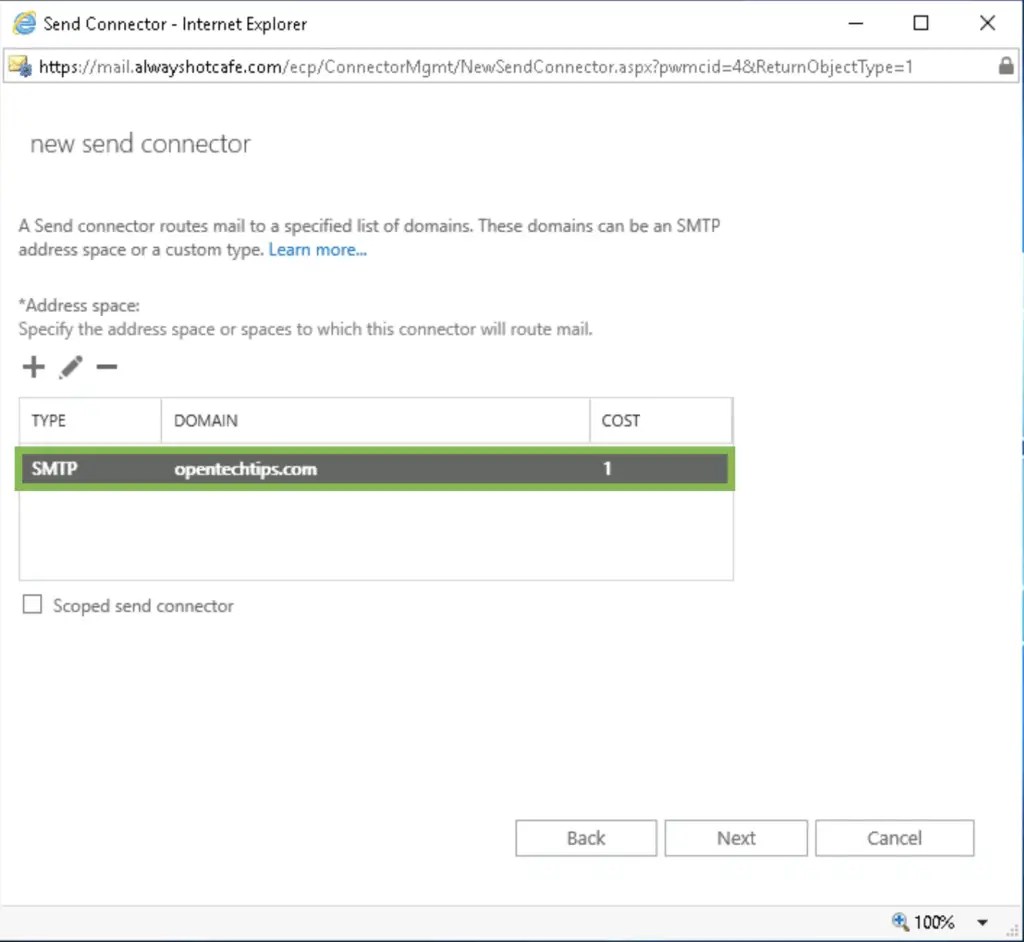
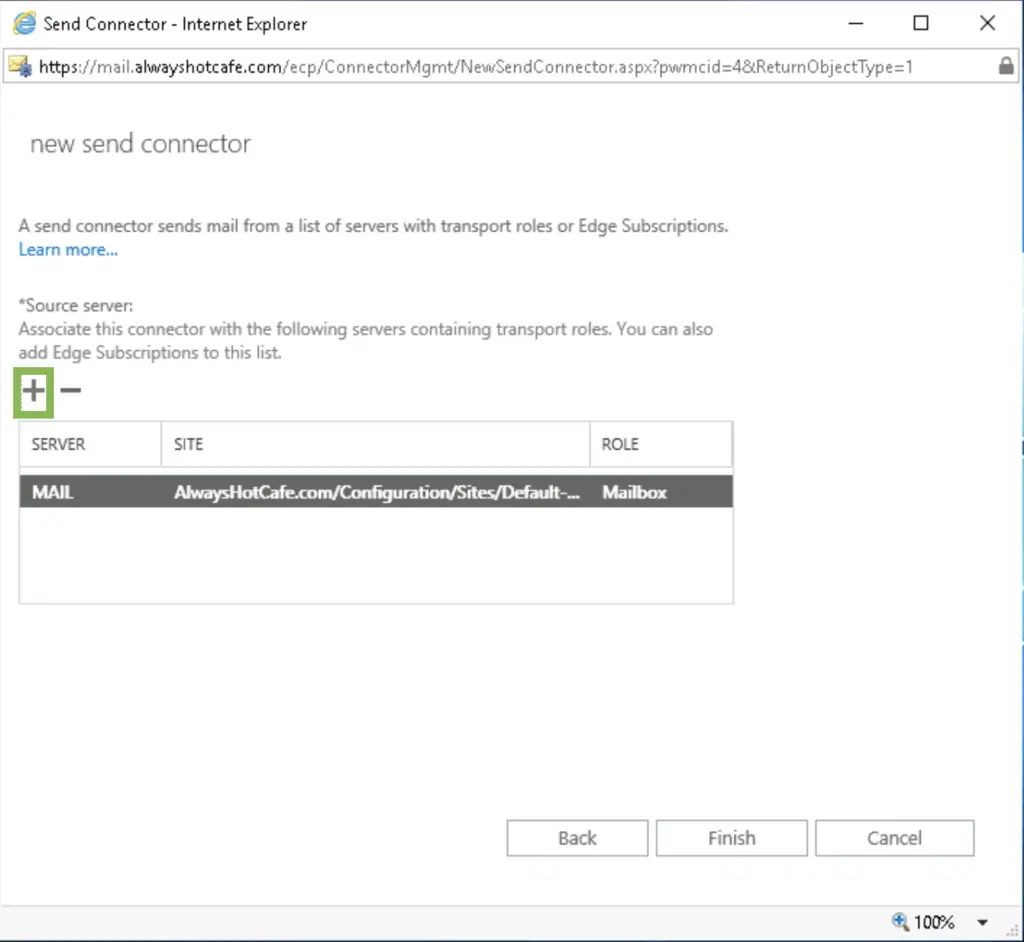
Add the mailbox servers that are allowed to use the connector, then click on finish.
Enforce Received TLS
We can also enforce TLS on received emails
# Enforce on all MailBox servers
Set-ReceiveConnector "*\Default Frontend MAIL" -RequireTLS:$true
# Enforce only on the MailBox server called: MAIL
Set-ReceiveConnector "MAIL\Default Frontend MAIL" -RequireTLS:$true

Comments