The task for today is to join a Microsoft Active Directory domain with our CentOS box.
We use the sssd package to accomplish this, first we start with a basic CentOS installation, we go through the initial setup, then the joining process, lastly, we log in with a domain user to the box.
Before You Begin
We will be working with the following configuration
| Domain to join: | jd0e.com |
| Domain Contoller: | DC.jd0e.com |
| 10.0.1.1 | |
| AD user account: | JD0E\admin |
| RHEL computer: | CentOSBox |
| 10.0.2.10 |
Make sure your computer hostname is added to the AD DNS system. It is not critical but adds consistency to our network.
It is critical is to add a domain controller to the /etc/resolv.conf file as this is needed for the CentOS box to find the AD server and initiate the domain joining process.
# Change the username and domain locally
echo CentOSBox.jd0e.com CentOSBox | sudo tee /etc/hostname
# Add the AD domain controller as the DNS server to query
echo nameserver 10.0.1.1 | sudo tee /etc/resolv.conf
# Reboot the server
sudo reboot
1. Install sssd and the required packages
We need to have the following packages on our machine to take advantage of the AD authentication with kerberos, and have access to CIFS utils to mount windows SMB shares
sudo yum install -y sssd realmd samba-common krb5-workstation oddjob oddjob-mkhomedir sssd adcli
2. Joining the domain
We are going to join our jd0e.com AD realm with the JD0E\admin user account
sudo realm join --user admin DC.jd0e.com
After the command run we see if it was completed successfully
[john@CentOSBox root]$ sudo realm list
jd0e.com
type: kerberos
realm-name: JD0E.COM
domain-name: jd0e.com
configured: kerberos-member
server-software: active-directory
client-software: sssd
required-package: oddjob
required-package: oddjob-mkhomedir
required-package: sssd
required-package: adcli
required-package: samba-common-tools
login-formats: %U@jd0e.com
login-policy: allow-realm-logins
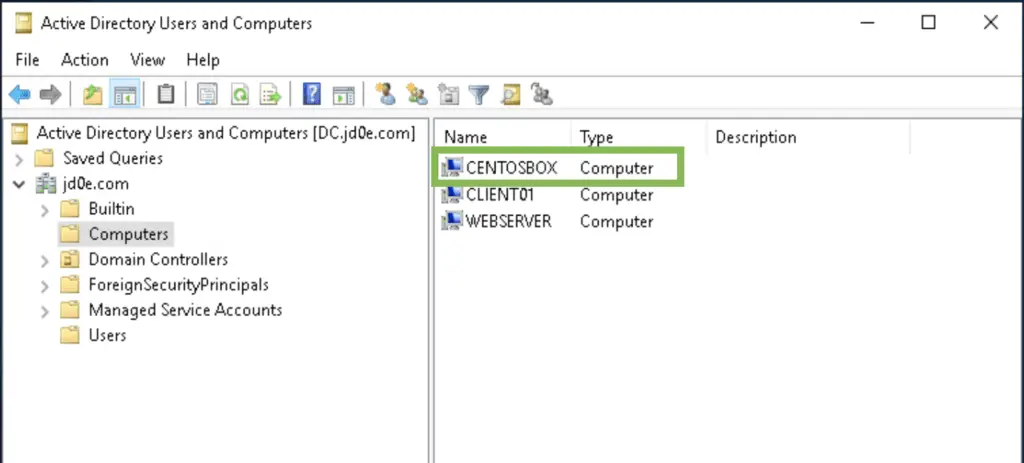
Excellent, we are a member of the jd0e.com domain now. We can even verify that the CentOSBox computer account appeared in the “CN=Computers,DC=jd0e,DC=com” container on our domain controller.
3. Tweak the sssd.conf file
As we use a single-domain environment we want the system to accept simple usernames without the domain specified or the FQDN format of the usernames being used, also say we want the JD0E\Domain Administrators group to have superuser rights on the CentOS box.
We edit the /etc/sssd/sssd.conf file accordingly
[sssd]
domains = jd0e.com
config_file_version = 2
services = nss, pam
[domain/jd0e.com]
ad_server = dc.jd0e.com
ad_domain = jd0e.com
krb5_realm = JD0E.COM
realmd_tags = manages-system joined-with-adcli
cache_credentials = True
id_provider = ad
krb5_store_password_if_offline = True
default_shell = /bin/bash
ldap_id_mapping = True
use_fully_qualified_names = False
fallback_homedir = /home/%u@%d
access_provider = simple
simple_allow_groups = Domain Admins
Now restart the ssd service
systemctl restart sssd
4. Make the [domain]\Domain Admins superusers
We also want the Domain Administrators in the AD system to have superuser rights, for that we create an additional config file for sudoers in /etc/sudoers.d and add the “domain admin” group there
vi /etc/sudoers.d/sudoers
%domain\ admins ALL=(ALL:ALL) NOPASSWD:ALL
5. Add the CentOS server to the AD DNS system
Not a critical step but it’s nice to add the CentOSBox A record to the jd0e.com zone.
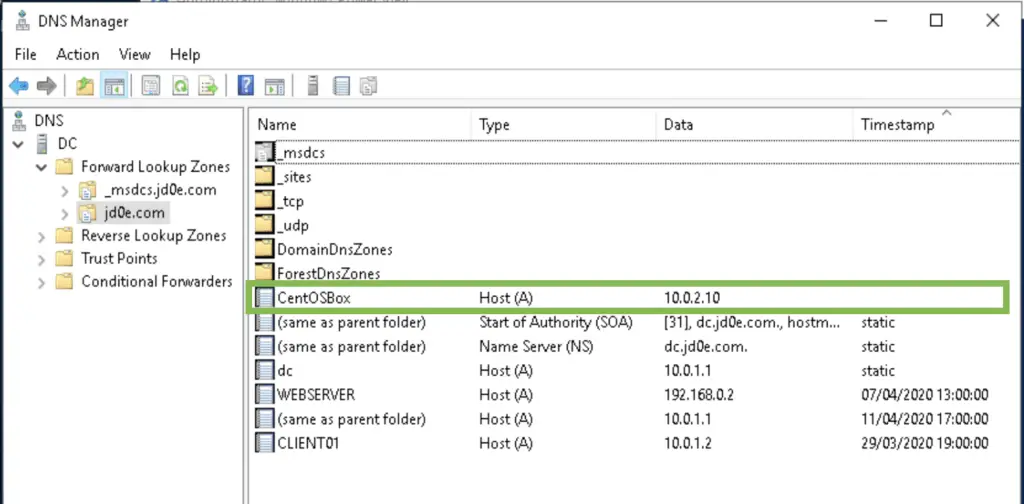
It will make administration easier later as we don’t need to remember the IP address of the box, the name will be enough: CentOSBox.jd0e.com or simply using the NETBIOS name on a domain computer: CentOSBox
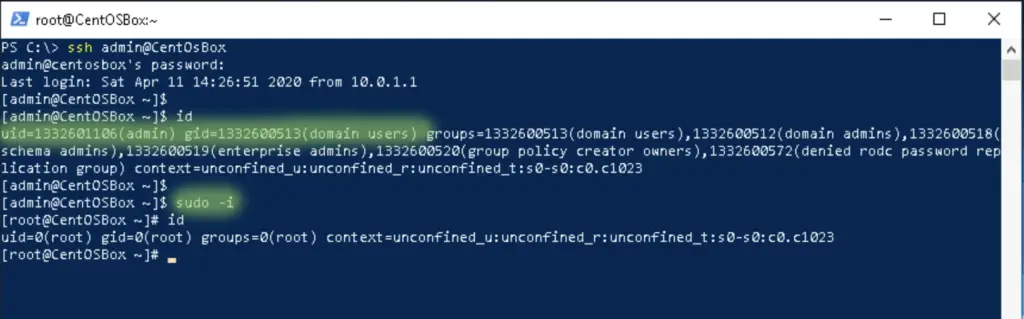
6. Log in with a domain account
We log in to the linux box with the admin@jd0e.com admin account, and make sure it has superuser rights 🙂

Comments