There might be scenarios when cutting ADFS and falling back to cloud authentication is urgently required. For example, when our on-premises ADFS authenticator servers go down - possibly due to a network outage - we want our users to be able to authenticate again. Remember, with ADFS the users are authenticated on the dedicated, on-premises authenticator servers. If those boxes are not accessible, our users won't be able to log into their mailboxes, or any other cloud services.
The quick way to do fix the login is changing authentication to "managed" type in the cloud for the affected domain(s). This will let the cloud servers know to use the pre-synced user password hashes to authenticate users, using the cloud login forms (see step 2).
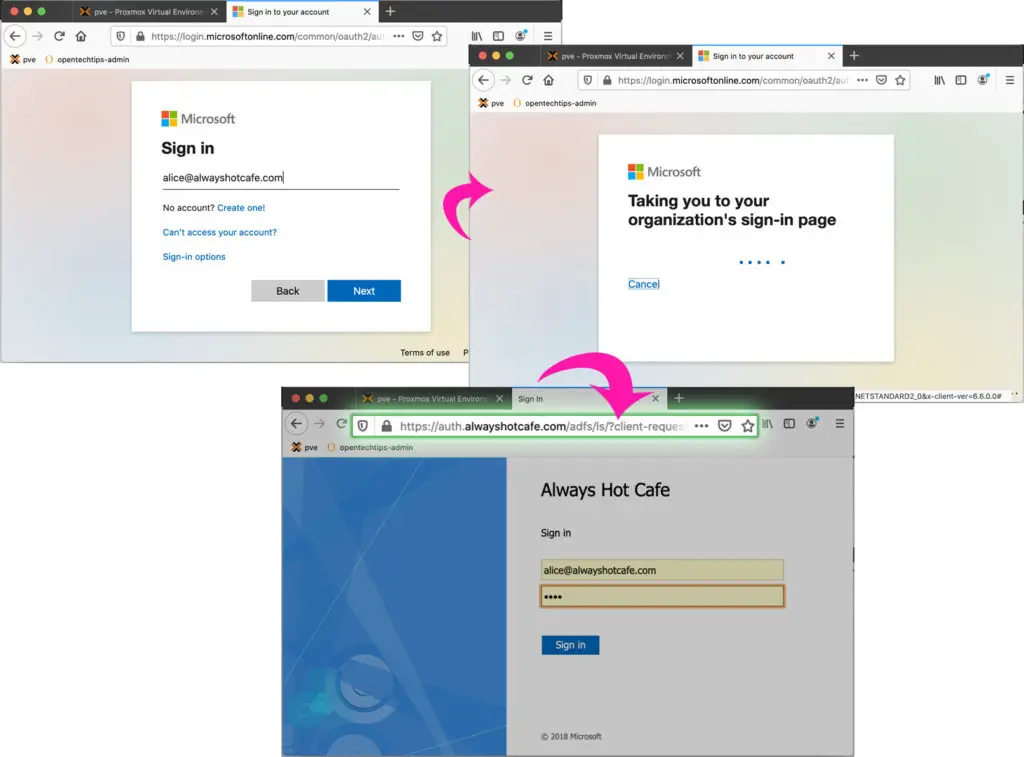
1. Authentication with ADFS - Before Cut
Here is a simple example to visualize the authentication process with ADFS being set. Alice tries to authenticate from the internet. In this setup, after the cloud senses that she is using a federated domain ( @alwayshotcafe.com ) it bounces her request straight to the on-prem authenticator server: auth.alwayshotcafe.com. After successful login, the user will be allowed to use resources in the cloud.
2. Switch to Cloud-Managed Authentication
Our goal is to make the cloud server do the authentication process. First, we connect to MS Online from a domain server. In our example we use our domain controller (DC.alwayshotcafe.com). Detailed steps are here Then run the following instructions to disable ADFS.
PS C:\> Set-MsolADFSContext -Computer adfs.alwayshotcafe.com PS C:\> Convert-MsolDomainToStandard -DomainName alwayshotcafe.com -SkipUserConversion:$true -PasswordFile c:\temp\passwdfile.txt Successfully updated 'alwayshotcafe.com' domain. # If access to the ADFS server is lost, use this command instead of the first two: PS C:\> Set-MsolDomainAuthentication -Authentication managed -DomainName alwayshotcafe.com
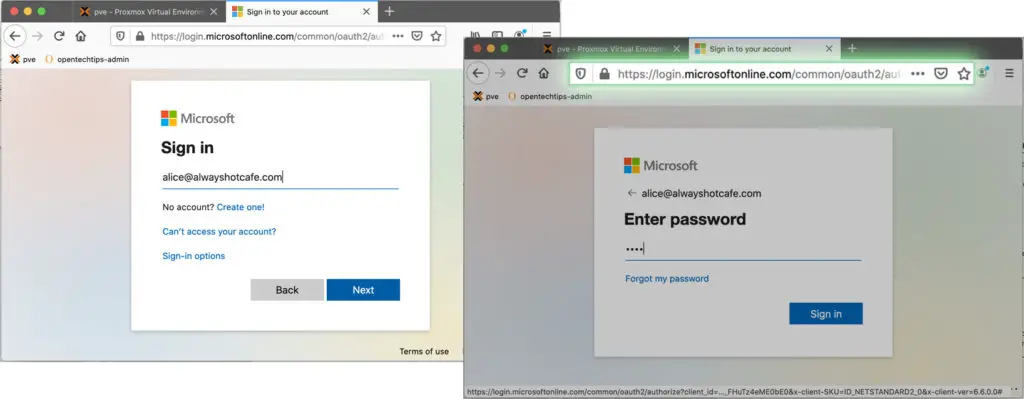
3. Verify authentication
After the steps above, when Alice tries to log in next time, she will get the Office365 cloud login form instead of the on-prem ADFS landing page!

Comments