Deploying DKIM on Zimbra Collaboration Edition Server is simple compared to the difficulty of doing so on an on-premises Exchange server. As it's built into the suit, we have an easy job creating the key pairs with a single command. The command immediately shows us the record that needs to be added to the public DNS (MAKE SURE YOU REMOVE THE LINE BREAKS WHEN PUBLISHING THE RECORDS! Details below
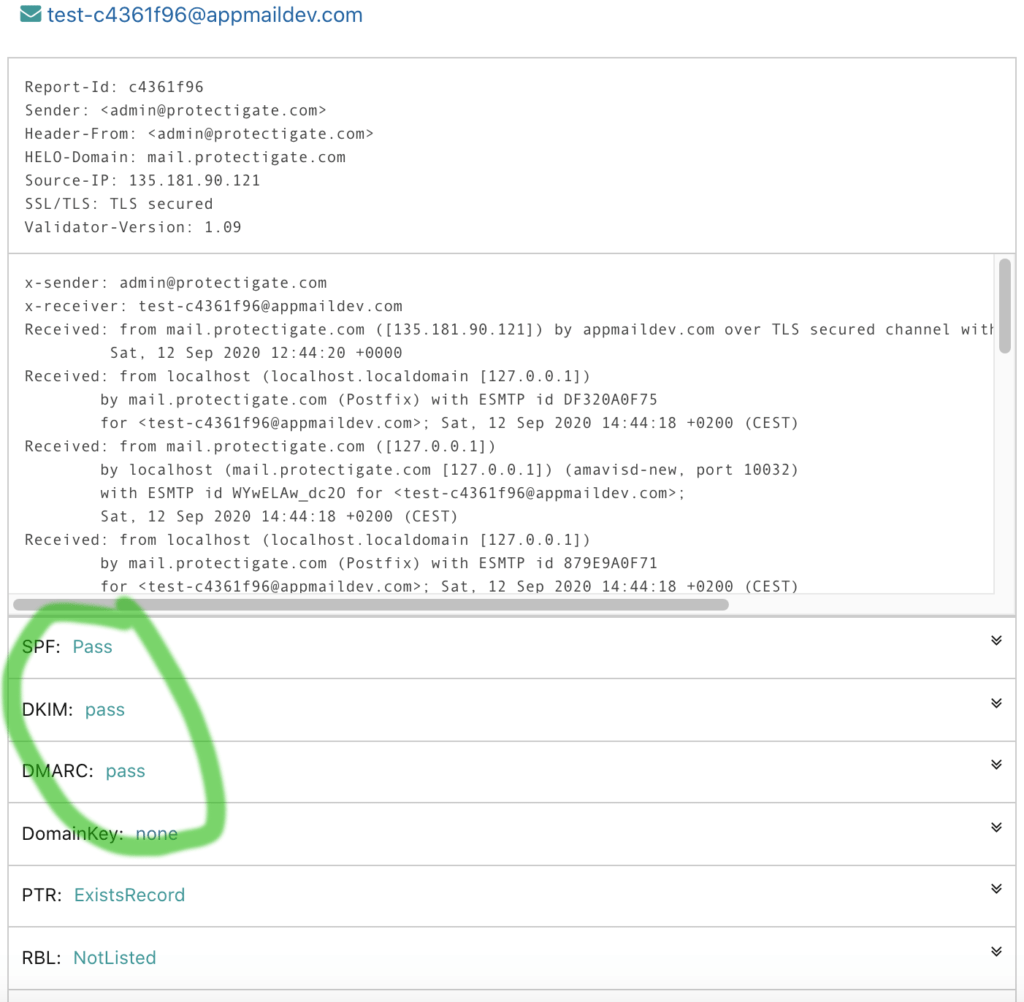
After DKIM for our domain is set and ready to go, we verify that it's working using online tools like the excellent DKIM validator from appmaildev (step 3)
1. Create DKIM keys on the server
# Add DKIM data to our domain on the Zimbra server, generating a 2048 bit key, using custom selector called: s1 # Run the command AS THE 'zimbra' USER! [zimbra@mail ~]$ /opt/zimbra/libexec/zmdkimkeyutil -a -b 2048 -s s1 -d protectigate.com DKIM Data added to LDAP for domain protectigate.com with selector s1 Public signature to enter into DNS: s1._domainkey IN TXT ( "v=DKIM1; k=rsa; " "p=MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEA2uChMOLHL7IGewJQ3ZmrxJU3oiUtr9ardljovG/B4PLFh5Aq2x8fCkSZyvyor7Ditc1HAf66PyNkiC4XqFeGK0HGuqBnpjAu6NvF+3nuNo2HRZf6oQYOB0HypBTtkc9cTBCjzw73kAxMws9+UUlW/0eKIlHHDfkud5AKIwj78Zv4XVQ1hKl/neVrTtgvd5szP+iKtbwXs/bNIw" "jbt8ZexlcaV/5wHZCeM9yIc4K9izS7KKHGw+xAyy3bCV/sQ0tWOldJ+YK4BtPEjdm2prs9AUaKwIzuqu3hpV1hGREO3CjS21zMUG8Pr7vXIV1g0rGPJxCmTW+w9tuj49czYq/S1wIDAQAB" ) ; ----- DKIM key s1 for protectigate.com [zimbra@mail ~]$
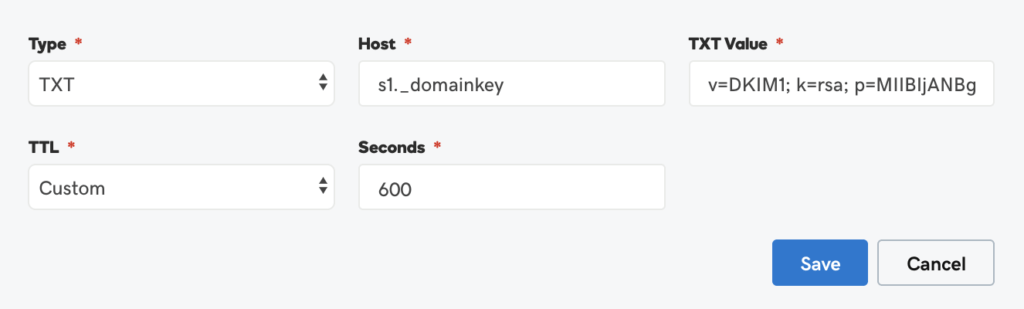
2. Add public DNS record
Use the info from the command output from earlier, but don't forget: the whole record with the v= (version), k= (key algorithm) and the whole private key after p= is a SINGLE LINE!
# DKIM TXT record as follows: Host: s1._domainkey Value: v=DKIM1; k=rsa; p=MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEA2uChMOLHL7IGewJQ3ZmrxJU3oiUtr9ardljovG/B4PLFh5Aq2x8fCkSZyvyor7Ditc1HAf66PyNkiC4XqFeGK0HGuqBnpjAu6NvF+3nuNo2HRZf6oQYOB0HypBTtkc9cTBCjzw73kAxMws9+UUlW/0eKIlHHDfkud5AKIwj78Zv4XVQ1hKl/neVrTtgvd5szP+iKtbwXs/bNIwjbt8ZexlcaV/5wHZCeM9yIc4K9izS7KKHGw+xAyy3bCV/sQ0tWOldJ+YK4BtPEjdm2prs9AUaKwIzuqu3hpV1hGREO3CjS21zMUG8Pr7vXIV1g0rGPJxCmTW+w9tuj49czYq/S1wIDAQAB
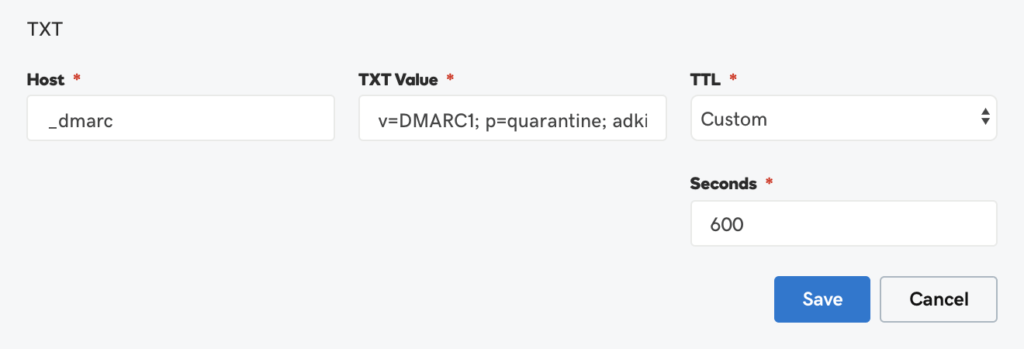
And to cover everything we create a DMARC record to check all messages and quarantine them if either SPF or DKIM fails:
3. Test the key
Last step is to test the key first on the server:
/opt/zimbra/common/sbin/opendkim-testkey -d protectigate.com -s s1 -x /opt/zimbra/conf/opendkim.conf
Then we use DKIM test tool in below, where you can either send the test server a test email to analyze the SPF, DKIM and DMARC setup, or copy in the header of an existing email message for verification.

Comments