Installation
In Exchange Online DKIM is a built-in service, but on an on-prem Exchange 2019 deployment we need a 3rd party application to add this functionality to our Exchange infrastructure.
In this guide we use Stefan Profanter's excellent dkim-exchange application for this purpose, which is available here: https://github.com/Pro/dkim-exchange/releases/latest
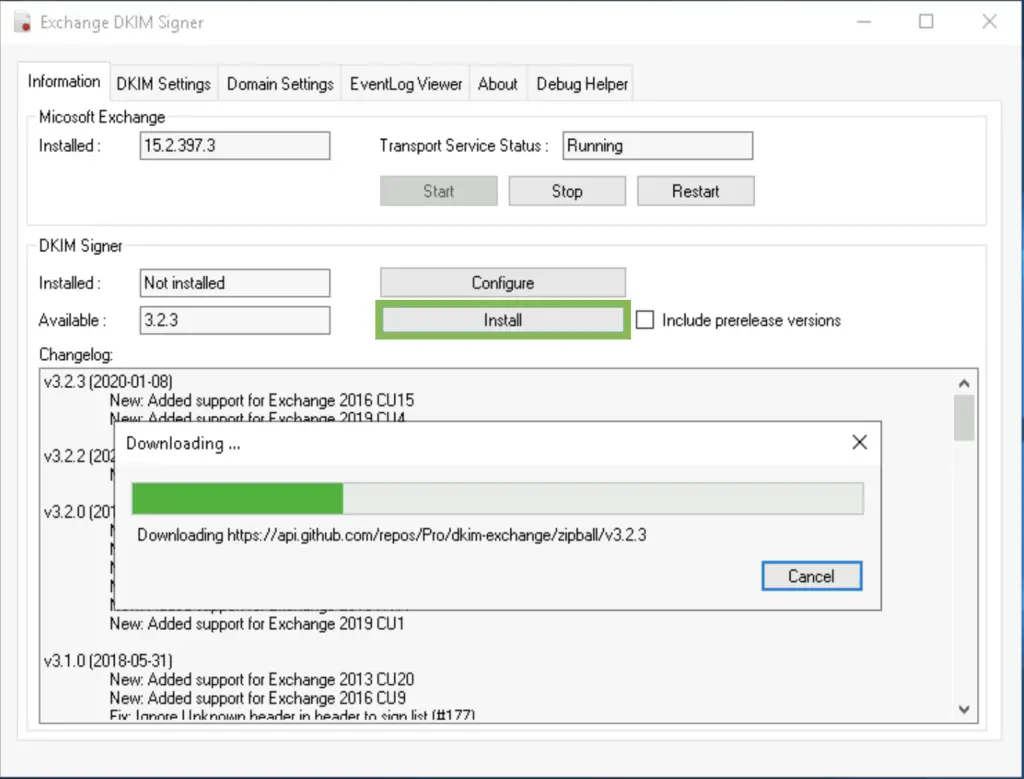
After installing the program, we open Configuration.DkimSigner.exe
and click on the "Install" button, or download the installer straight from https://codeload.github.com/Pro/dkim-exchange/legacy.zip/v***
Configuration
After installation finished, open the configurator.
C:\Program Files\Exchange DkimSigner\Configuration.DkimSigner.exe
Click on the "Configure" button and move the DkimSigner agent to the very bottom of the list.
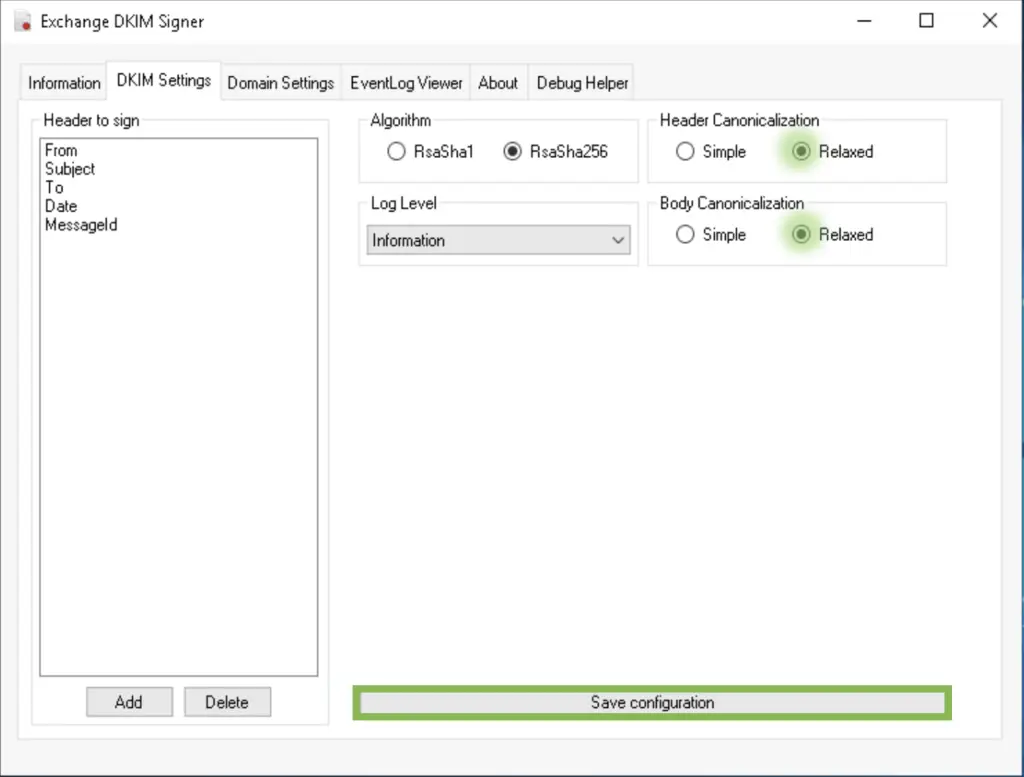
Under the DKIM settings tab select relaxed canonicalization as Exchange tend to add, remove and change whitespaces (spaces, tabs, new lines) when processing and submitting messages. This is a problem, as DKIM creates a hash signature of the original message body and header, then when received, the recipient server will create those hashes too and compares the two versions. They need to match.
Simple canonicalization requires the body and header of the messages to be identical when comparing the original message and the received version. Relaxed canonicalization gives the transport agents more flexibility in changing messages, it replaces all whitespaces with a single space character, converts all characters to lowercase, removes heading and trailing whitespaces, etc.
On the "Domain Settings" tab we add our domain name, the DKIM selector name will be selector1.
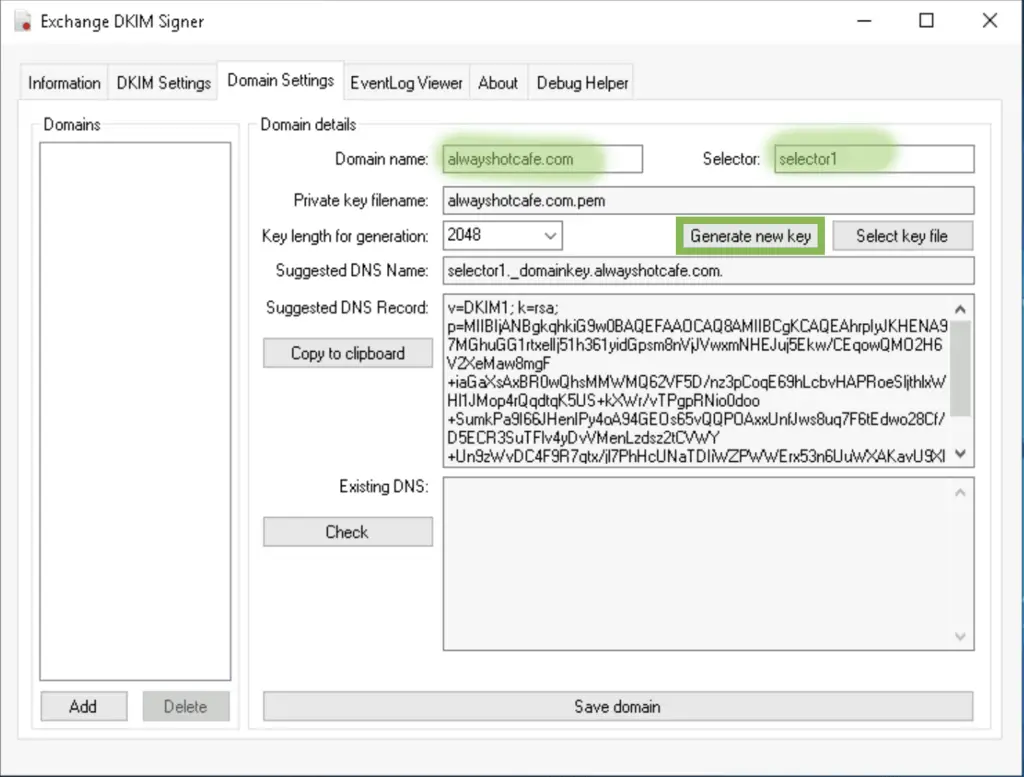
The private and public keys will be generated. The server encrypts the hashes with the private key, the clients will use the public key to decrypt that hash. This proves authenticity as only the server can generate this encrypted key, if someone modified the message in transit they could re-generate the hashes of the new body and header, but the cannot encrypt the hash like the server do.
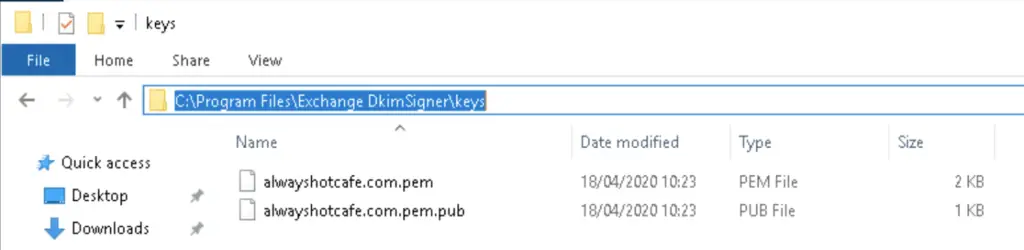
Publish the selector DNS record for DKIM
The public key is published in the p= part of the DNS record that we add the domain public zone file, in our example at GoDaddy.

Restart the service
How it works
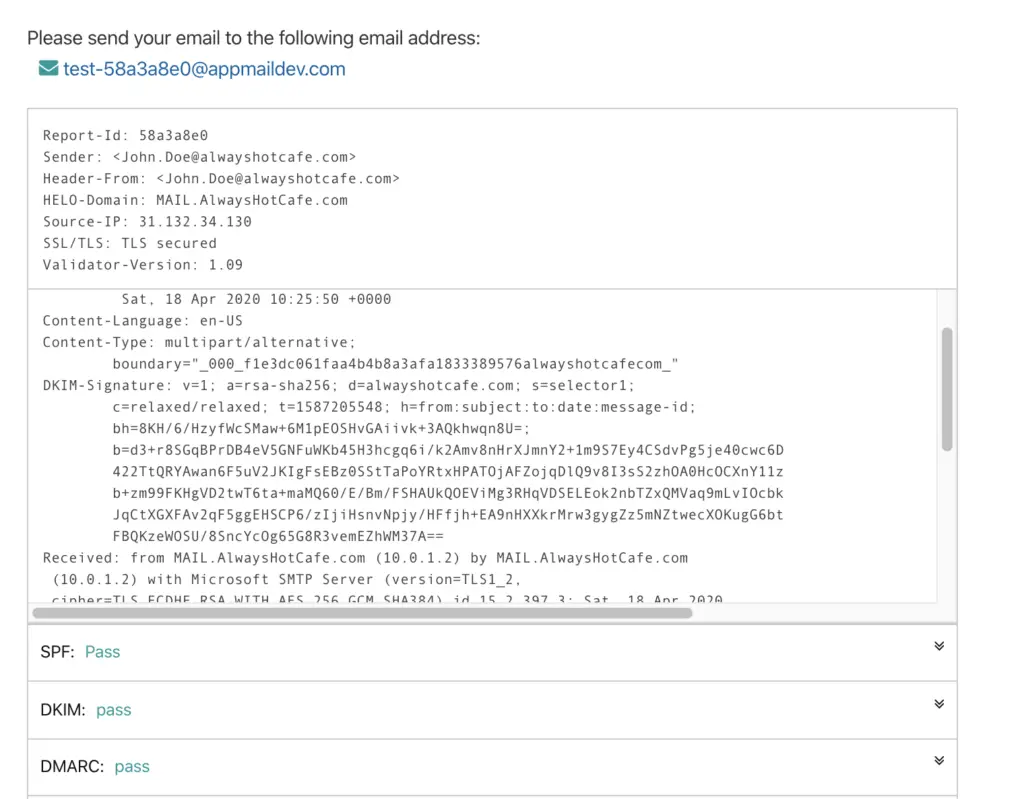
John Doe from Always Hot Café sends me a message to zsolt@opentechtips.com. The header of the received email contains a section called DKIM-Signature. The s= part tells my client that the dkim selector is selector1, that means the client will check the selector1._domainkey.alwayshotcafe.com TXT record, which contains the public key with which the client is able to decrypt the two hashes under the b= and bh= parts.
Received-SPF: Pass (protection.outlook.com: domain of alwayshotcafe.com
designates 31.132.34.130 as permitted sender)
receiver=protection.outlook.com; client-ip=31.132.34.130;
helo=MAIL.AlwaysHotCafe.com;
Received: from MAIL.AlwaysHotCafe.com (31.132.34.130) by
LO2GBR01FT003.mail.protection.outlook.com (10.152.42.89) with Microsoft SMTP
Server (version=TLS1_2, cipher=TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384) id
15.20.2921.25 via Frontend Transport; Sat, 18 Apr 2020 09:48:28 +0000
Content-Language: en-US
DKIM-Signature: v=1; a=rsa-sha256; d=alwayshotcafe.com; s=selector1;
c=relaxed/relaxed; t=1587203307; h=from:subject:to:date:message-id;
bh=3ECfkrEiARfvXNGT95TLaUGgi50dOXnbyEyBN92OL7I=;
b=ezzdjkLHWh038rZ2rzGtOK8iDkICzeabakYi7WMNFb362wrSZ9BakHhjjca5a/+oqKbwGO9fA59
nshOeqvy6AzwuT7B3gPJPJ6kAaTXu6T8L5GYjeJaWm5T5Gk9/gxaDJxMqtM9JCt+w6wUN6xfjjRgW
fRQrkM4GJ5WUs+tPJ+KGWn9nyIU01VeFPwnPx7xlXCfKrTjmRhaAu0hyPNviO/MdvEqCMUZA+3tVk
1YAZ6xwL4c6SLx8N1zK88O/0Uk6gnQItG4UcYsxJ2+/Z0Jk0MMnNDpvvJGkpo34HAkuWXg74m70oY
zcI+mTn/lM2yPJzu6fJ+/HBZ/rnfDins6nOw==
Received: from MAIL.AlwaysHotCafe.com (10.0.1.2) by MAIL.AlwaysHotCafe.com
(10.0.1.2) with Microsoft SMTP Server (version=TLS1_2,
cipher=TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384) id 15.2.397.3; Sat, 18 Apr 2020
10:48:23 +0100
After having the original hashes, the client goes through the same hashing process, using the algorithm specified it the a= part.
If the newly generated and the earlier decrypted hashes match, the DKIM test passes.
TEST
https://www.appmaildev.com/en/dkim is a great website to verify that DKIM works.

I am using exchange 2019 cumulative 5 PRO/DKIM install ok, generate the key ok but after add my public dns to DKIM record now working, when checking the mx toolbox showing an error has occured. Please explain me what is this issues
Hi Zayar,
Please let me know the domain name you are using and I try to help you troubleshoot the issue with DKIM
Hi Zayar,
DKIM seems to be working fine, the part the signature is failing is the body hash. This usually means that the body is changed AFTER the DKIM signature is calculated. Most of the time it is a disclaimer or footer that is automatically added to messages, like you do have in your test email.
If the Exchange server appends this with a transport rule, just make sure the “Exchange DKIM Signer” agent is moved to the very top of the agent list (see the article, under the Configuration part).
If it is appended by a 3rd party provider, DKIM needs to be deployed and set on their servers.
Z.
Ok, I am confused a little. The “selector1” you have at the stop is that supposed to be left alone or is that supposed to be your domain suffix like “mail” or whatever you use to for mail server?
Hi, “selector1” is an arbitrary name you pick for the DKIM record. It can be anything you like. If you choose “blahblah”, and your domain name is “smoothrunnings.ca”, then you want to set up the corresponding TXT record under the name: “blahblah._domainkey.smoothrunnings.ca”. After setting everything up every email that leaves your server will contain the reference to the “blahblah._domainkey.smoothrunnings.ca” public TXT record that contains the actual public key which can decrypt the hashes also stored in the header. Please see the “How it works” section in the article.
Dear,
Im a newby on this part so sorry if my question is stupid, only if i use this for mutiple domain should also create mutiple selectors, for example three domains. henk.net henk.com and henk.org selector 123?
Many thanks for your help and time
Yes correct, for each domain you need a different selector.
Where you say “Click on the “Configure” button and move the DkimSigner agent to the very top of the list. The DKIM sugner will run first when submitting emails.”, this is wrong. It needs to be at the bottom. It even says that in the dialog you show.
Hi. Please I have a question. When I Try to generate the new Key, the Dkimsigner only generates a .pub file. It never generates a .pem file, Please, I must to generate or setup any other process?
In DAG and server cluster shall the DKIM Signer be deployed on each server? How about the keys? Shall they be generated on first server and copied to each server in cluster?