Active Directory is a device and user management system that is stored and maintained across the network by a network of dedicated servers, called Domain Controllers (DC).
To maintain the proper functionality of the system, certain functions need to be managed by nominated servers.
Below we take a look on these roles, what they are doing and what happens if they fail.
What are the Flexible Single Master Operation (FSMO) Roles and What They Do?
- Domain Naming Master: responsible for adding or removing domains to the existing forest
- Schema Master: controls the modification and updates to the schema
- RID Master: allocates SID ranges to domain controllers within a domain
- PDC Emulator: responsible for account password changes, manages lockouts, registers GPO changes and synchronizes the network time across the domain
- Infractructure Master: responsible for referencing SIDs and object names in other domains
Why Do the FSMO Roles Exist?
After establishing roughly what each of those roles are for, it's time to dig a little deeper in the topic and see why these roles are actually so important.
We can think of Active Directory as a dynamic database. It stores user- and computer accounts, authentication information, all kind of policies, etc. Each of the domain controller servers have a copy of this information (or part of it) stored and they communicate periodically with each other to maintain the consistency of the data.
Now, here's the catch: for certain type of data Active Directory follows a multi-master model, meaning data changes can happen on any member servers. These servers communicate and replicate changes every 180 minutes by default.
Think about this: let's say an admin decides to change a user's telephone number on a domain controller in Washington, and at about roughly the same time another admin changes the same user's phone number in New York to a different one, as he's working from an older phone list.
What happens then? Because of the multi-master model, the next time replication occurs in the system, the time stamp of the change is checked and the last change wins. That simple. Now, for a telephone number, this is not a big issue.
But there are cases when it's very important to avoid conflicting updates. For example, changing a user's password after the account was compromised. it's critical to have that information immediately and centrally circulated in the whole system.
For this reason, critical data can be updated only on a dedicated machine, in a single-master fashion. Very early on a single server, the primary domain controller was given this power.
Later the roles of the PDC was divided into five separate master roles, which all can be assigned to separate servers to avoid having a single point of failure. The FSMO roles were born.
FSMO Roles Detailed
Domain Naming Master
The domain naming master server has the duty of checking if a newly added domain is unique in the forest. Also, it's needed when removing domains from the infrastructure. As such, there's only one server having this role in the entire forest. If the role is seized from the master domain controller, it cannot be added back to the original server even if it was successfully restored after the seizure. In case it's important to add the role back to the original server, it needs to be reinstalled first.
Schema Master
This role is needed when making any modifications or upgrades to the schema of the organization. The schema gives the skeleton of the object structure in AD. For example it dictates what attribute an AD user account can have, such as the user's first and last name, telephone number, primary email address, etc.
Upgrades happen to the schema when a new version of Exchange server is deployed as each version introduces new attributes, and objects to AD.
RID Master
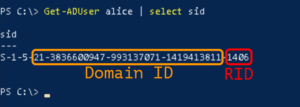 Stands for Relative ID master, there is also only one of this server in the whole forest. Each Active Directory objects have a SID. The RID part is the last few numbers of those SIDs.
Stands for Relative ID master, there is also only one of this server in the whole forest. Each Active Directory objects have a SID. The RID part is the last few numbers of those SIDs.
Like take S-1-5-21-3836600947-993137071-1419413811-1406 as an example. Here 1406 is the RID component of the identifier, the first part is specific to the account type and the domain.
Each new object in AD receives a unique RID when they are created. The RID master has the role of allocating 500 chunks of RID numbers for domain controllers in the domain, that they can use when creating objects. When they run out of all available RID numbers, they ask more from the RID master.
PDC Emulator
This role is if not the most important but the most noticeable when it's not functioning correctly. The PDC emulator is the main server when it comes to password management: it has the sole authority to change passwords in the domain. Account lockouts also managed by the PDC emulator when trying the wrong password too many times.
Also, the holder of this role commits GPO changes and controls the network time service for all the servers in the domain. This is extremely important, as the Kerberos system that is used for the single sign-on functionality in the domain relies on accurate time for the tickets it generates. If there is a 5 minute or larger discrepancy on two computers, Kerberos would fail.
Infrastructure Master
The IM is responsible for updating object references locally. The IM keeps certain information of objects from other domains. For that purpose it creates so called phantom objects in the local domain.
These phantom objects basically contain the distinguished names, GUID and SID of the foreign accounts, and if those accounts are added to groups or are used in ACLs in the local domain, the proper names and attributes are displayed for those accounts. If accounts from foreign domains show up with only their SIDs, that's a sign of the IM failing.
Important: the IM role should not be assigned to a server that is a Global Catalog server at the same time! The IM's job is to periodically compare objects of the local domain against objects in other domains in the forest. It's looking for changes between it's own database and an available global catalog that is ideally a different server in the domain.
If the IM itself is a global catalog (that has all the updated account information at all times) it never thinks that there is a change and never issues any updates. It's not an issue if there is only one domain in the forest, or if all the domain controllers are global catalogs though.
Authority: Forest or Domain
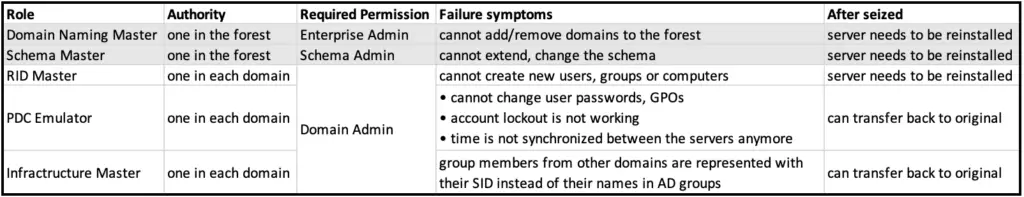
Two of them, the Domain Naming Master and the Schema master are specific to the whole forest. That means even if the AD system contains many domains there is only one domain controller which holds these roles.
The other three roles are specific to each individual domain, meaning if we have three domains in the AD system then there will be three of each of these roles.
Query the role holders
Use the netdom command on a domain controller to check the master role holder server for each roles.
PS C:\> netdom query fsmo Schema master DC.a.com Domain naming master DC.a.com PDC DC.a.com RID pool manager DC.a.com Infrastructure master DC.a.com The command completed successfully. PS C:\>

Comments