We established in part1 why the key exchange takes place, if you missed that part click HERE to check it out.
Basically the client and the server agree on a key that they can use to encrypt the rest of their communication. Let’s see how that key exchange happens exactly.
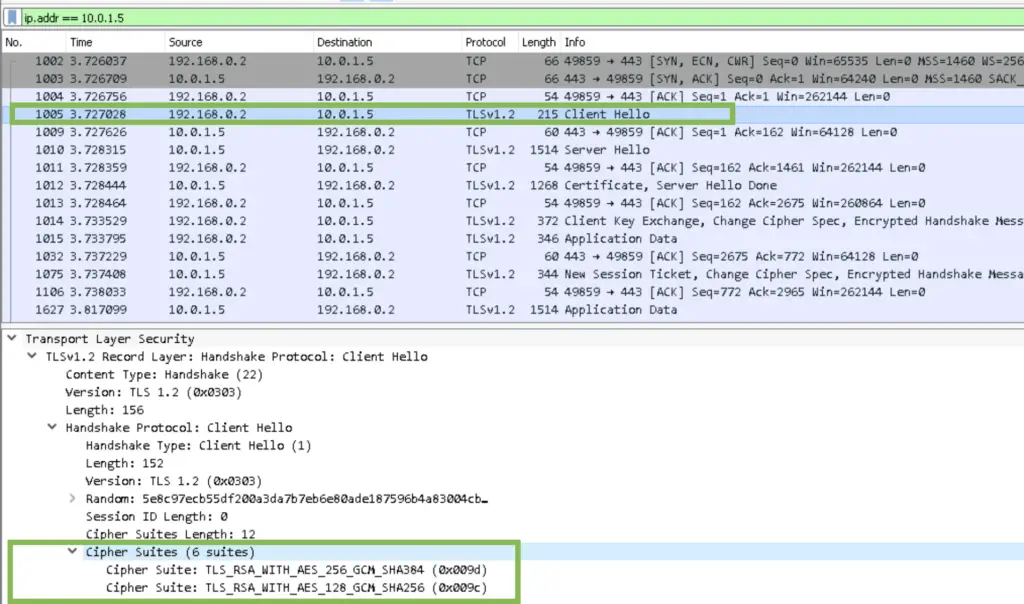
Step 1: Client Hello
After establishing the TCP connection, the client initiates the TLS channel by sending the TLS cipher suites it supports. In our case it supports six
2. Server Hello
In response, the server greets the client back and picks up one cipher suite to be used later.
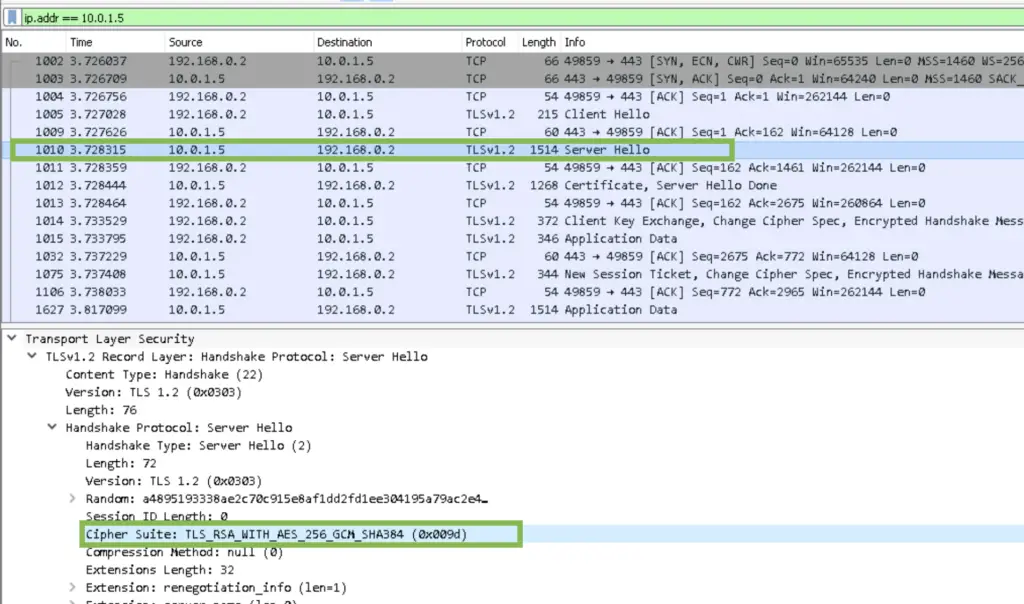
The suites describe three main protocols, aspects. Here the server picked RSA for key exchange - to negotiate the secret key for the next part – the second is the symmetric encryption algorithm for the rest of the messages, AES256. The third one is the hashing algorithm for ensuring the messages were not tampered with.
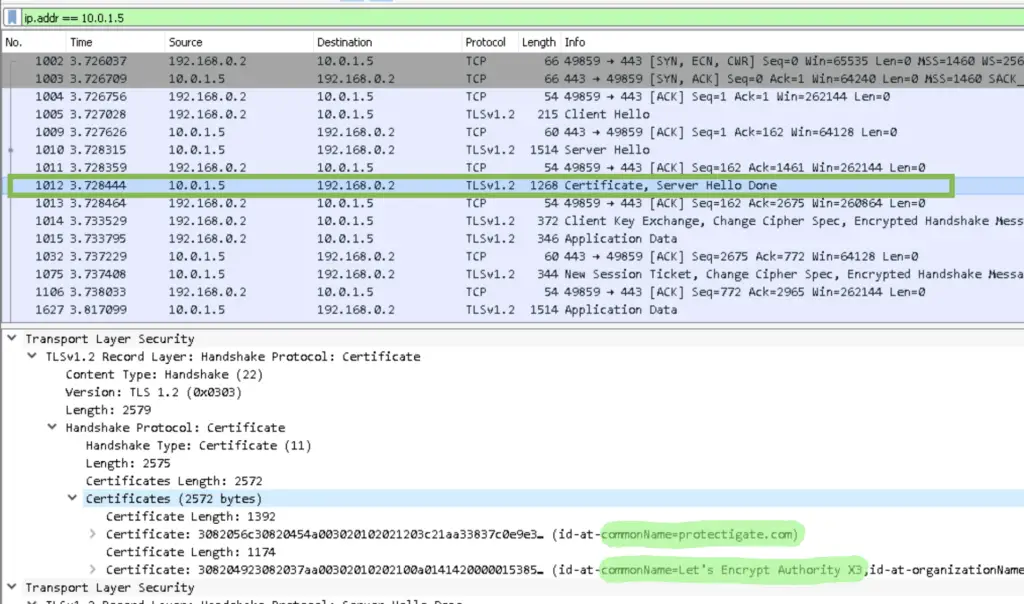
3. Certificate is Sent (from server to client)
Next, the server sends its SSL certificate that contains the public key together with the signing CA’s signature to the client and the rest of the certificate chain. That contains the Root CA certificate, in this example it is "Let’s Encrypt Authority X3"
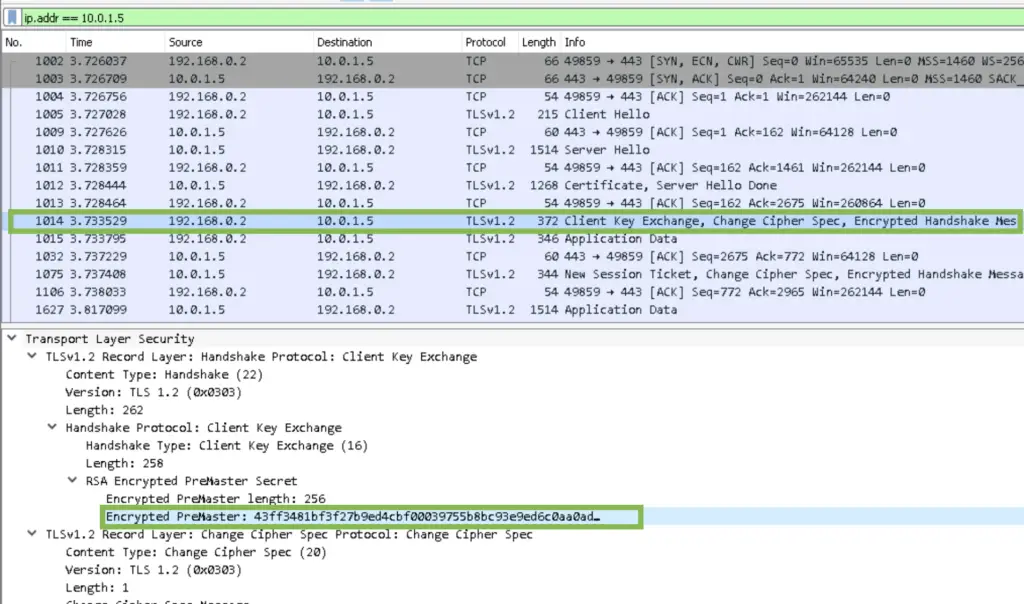
4. Secret Key (or session key) Exchange
This is the key step. The client uses the private key to encrypt a 256bit long secret key (for the AES256 protocol to be used later) which the server decrypts with the private key. Now they both know the secret session key.
After acknowledging and confirming the key, now they are communicating using AES256 encrypting-decrypting with the same secret they share now.

Comments