So you want to us SSH certificate authentication as opposed to password authentication. You add the client's SSH public key in the authorized_keys file on the server (as this guide shows), but when trying to connect you are still prompted for the password?
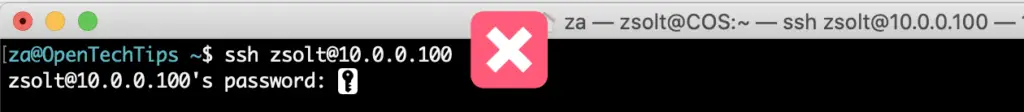
It's likely there is an ownership or permission issue with the authorized_keys file. Ideally the owner should be the user who's account is going to be accessed, but most importantly the permissions on the file should be lower than 777.
Example
We want to log into a CentOS linux machine called COS using a local user account on the server with the name of Zsolt. Here are the basic troubleshooting steps that likely will sort our issues:
1. Check the client's SSH public key we use
On our client open the hidden .ssh directory in your user profile (it's present even on Windows machines), and open the id_rsa.pub file:
Client public key:
za@OpenTechTips ~$ cat ~/.ssh/id_rsa.pub ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQC0+FccsKiWF4gPO4ZB9MQeRH/j5sOCdkFn+b+C9FRO2D86HYhlPhHJFjWasUrPo7O6PVSGxetG36kJ1REdtmmSzues1gKvl9YJxRkiCe2ML53f3l1Amg9BjYpDD45b/V4lZbxaspA5uF0IxmfrWy6uWKQ9nCdeFbgj1iXU/rGkyYv6bTkjNA3eBLjpdJqDnZ8FmYBp9Koxg4mQG8W8Sf3cqjklCbDzH0E9PZiBBLBl2qrJtO6VTum/ym8YF72rANkItz0c7L1s4hWmosWoH5AWWpy/NUffyxtBbkywn0EiCupAeXRU7bMNHltlkE2Iin+HU1jC3OspPlSuBMszpuLN zsoltagoston@Zsolts-MacBook-Pro.local
Check if it is present in the authorized_keys file in the user profile we are attempting to log in:
[root@COS ~]# cat /home/zsolt/.ssh/authorized_keys ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQC0+FccsKiWF4gPO4ZB9MQeRH/j5sOCdkFn+b+C9FRO2D86HYhlPhHJFjWasUrPo7O6PVSGxetG36kJ1REdtmmSzues1gKvl9YJxRkiCe2ML53f3l1Amg9BjYpDD45b/V4lZbxaspA5uF0IxmfrWy6uWKQ9nCdeFbgj1iXU/rGkyYv6bTkjNA3eBLjpdJqDnZ8FmYBp9Koxg4mQG8W8Sf3cqjklCbDzH0E9PZiBBLBl2qrJtO6VTum/ym8YF72rANkItz0c7L1s4hWmosWoH5AWWpy/NUffyxtBbkywn0EiCupAeXRU7bMNHltlkE2Iin+HU1jC3OspPlSuBMszpuLN zsoltagoston@Zsolts-MacBook-Pro.local
If it's not there, simply add the whole key to the end of the authorized_keys file, save it and try to log in. If it still doesn't work, proceed to step 2.
[root@COS .ssh]# ll total 12 -rw-r--r--. 1 root root 419 Nov 1 17:07 authorized_keys -rw-------. 1 zsolt zsolt 2590 Nov 1 17:00 id_rsa -rw-r--r--. 1 zsolt zsolt 563 Nov 1 17:00 id_rsa.pub
If it's not owned by the actual user (like here it's owner by root), change the owner to the right user
[root@COS .ssh]# chown zsolt:zsolt authorized_keys [root@COS .ssh]# ll total 12 -rw-------. 1 zsolt zsolt 419 Nov 1 17:07 authorized_keys -rw-------. 1 zsolt zsolt 2590 Nov 1 17:00 id_rsa -rw-r--r--. 1 zsolt zsolt 563 Nov 1 17:00 id_rsa.pub
The permissions on the authorized_keys file cannot be 777 (rwxrwxrwx)! This is an example of a poorly set up SSH profile:
The Group, or the Other users cannot have write permissions. Set the perms on the file to maximum 755 (rwxr-xr-x). Preferably 644 (rw-r--r--) or 600 (rw-------).
Hint: Use 644 if the owner is root or some other user, use 600 if the owner of the file matches the profile owner (here it's zsolt)
[root@COS .ssh]# chmod 600 authorized_keys [root@COS .ssh]# ll total 12 -rw-------. 1 zsolt zsolt 419 Nov 1 17:07 authorized_keys -rw-------. 1 zsolt zsolt 2590 Nov 1 17:00 id_rsa -rw-r--r--. 1 zsolt zsolt 563 Nov 1 17:00 id_rsa.pub
4. Verify it's working
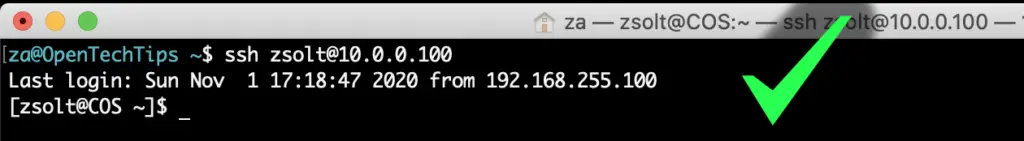
Enjoy!

Comments